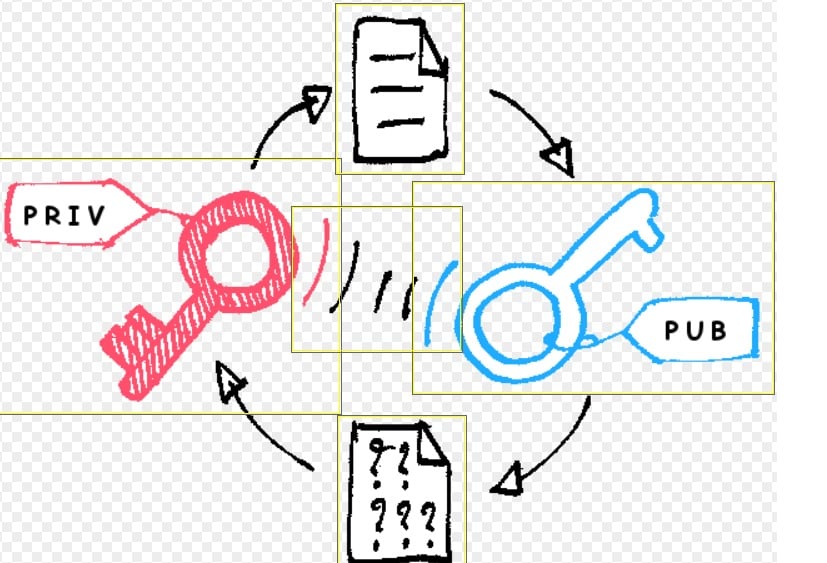
Best Encryption Software : The realm of digital security is paramount in safeguarding sensitive information from unauthorized access, and encryption software stands as a cornerstone in this endeavor. The best encryption software offers robust protection by scrambling data into unreadable formats, ensuring that even if intercepted, it remains unintelligible to unauthorized parties. From personal documents to corporate communications, encryption software serves as a vital layer of defense against cyber threats, data breaches, and privacy infringements.
One standout in the domain of encryption software is VeraCrypt, renowned for its open-source nature and robust encryption algorithms. VeraCrypt offers strong encryption methods such as AES, Serpent, and Twofish, providing users with a wide range of options to secure their data. Its versatility extends to various platforms, including Windows, macOS, and Linux, making it accessible to a diverse user base. Additionally, VeraCrypt supports features like hidden volumes and full-disk encryption, empowering users to safeguard their data comprehensively.
Another notable contender is BitLocker, integrated within the Windows operating system, offering seamless encryption for both individual files and entire drives. BitLocker utilizes AES encryption and offers features like multi-factor authentication and recovery keys, enhancing security and accessibility. Its integration with Windows ensures ease of use and compatibility, making it a popular choice for users seeking native encryption solutions.
For those prioritizing simplicity and convenience, FileVault on macOS provides seamless encryption for Mac users. FileVault encrypts the entire startup disk, protecting data at rest and ensuring confidentiality. With its integration into macOS, FileVault offers straightforward setup and management, making it an ideal choice for individuals seeking hassle-free encryption solutions on Apple devices.
In conclusion, the best encryption software plays a crucial role in safeguarding sensitive information from unauthorized access and ensuring data confidentiality. Whether it’s VeraCrypt’s robust open-source encryption, BitLocker’s seamless integration with Windows, or FileVault’s simplicity on macOS, users have a variety of options to choose from based on their specific needs and preferences. By leveraging encryption software, individuals and organizations can fortify their digital security posture and mitigate the risks posed by cyber threats and data breaches.
Defination Of Best Encryption Software
The term “best encryption software” refers to a category of digital security tools designed to encode sensitive data into unreadable formats, thereby safeguarding it from unauthorized access or interception. The primary objective of encryption software is to protect confidentiality and privacy by converting plaintext information into ciphertext, which can only be deciphered by authorized parties possessing the corresponding decryption keys. The best encryption software solutions typically employ robust encryption algorithms and adhere to industry standards to ensure the highest level of security. Additionally, they often offer features such as strong authentication mechanisms, seamless integration with operating systems or applications, and compatibility with various platforms and devices. Overall, the best encryption software provides users with a reliable means of protecting their data from cyber threats, data breaches, and unauthorized surveillance, thereby enhancing digital security and fostering trust in the confidentiality of sensitive information.
Importance of Best Encryption Software
The importance of employing the best encryption software cannot be overstated in today’s digital landscape, where data privacy and security are paramount concerns. Encryption software plays a critical role in safeguarding sensitive information from unauthorized access, interception, and tampering by converting it into an unreadable format, known as ciphertext. This transformation ensures that even if data is intercepted, it remains unintelligible to anyone without the appropriate decryption key, thereby preserving confidentiality and privacy.
One of the primary reasons for the importance of encryption software is its role in protecting data in transit and at rest. Whether data is being transmitted over networks or stored on devices or servers, encryption ensures that it remains secure and confidential. This is especially crucial in environments where sensitive information, such as financial data, personal records, or intellectual property, is constantly exchanged or stored.
Moreover, encryption software helps organizations comply with regulatory requirements and industry standards related to data protection. Many regulatory frameworks, such as GDPR, HIPAA, and PCI DSS, mandate the use of encryption to safeguard sensitive data and prevent unauthorized access. By implementing robust encryption solutions, organizations can demonstrate their commitment to compliance and mitigate the risk of regulatory penalties or reputational damage resulting from data breaches.
Furthermore, encryption software bolsters trust among stakeholders, including customers, partners, and employees, by demonstrating a commitment to data security and privacy. When individuals know that their personal information is encrypted and protected from prying eyes, they are more likely to entrust organizations with their data, fostering stronger relationships and brand loyalty.
In conclusion, the importance of the best encryption software lies in its ability to safeguard sensitive information, ensure regulatory compliance, and foster trust in the digital age. By employing encryption solutions, individuals and organizations can mitigate the risks posed by cyber threats, protect data privacy, and uphold the integrity of confidential information, thereby enhancing overall digital security and resilience.
Here Is The List Of 30 Best Encryption Software For 2024
- VeraCrypt ( Best Encryption Software)
- BitLocker
- AES Crypt
- 7-Zip ( Best Encryption Software)
- GPG Suite
- Symantec Endpoint Encryption
- FileVault (for macOS)
- Kleopatra ( Best Encryption Software)
- Boxcryptor
- Tutanota
- ProtonMail
- NordLocker ( Best Encryption Software)
- Cryptomator
- Enigmail
- PGP Desktop
- DiskCryptor ( Best Encryption Software)
- AxCrypt
- TrueCrypt (discontinued but still used by some)
- Sophos SafeGuard Encryption
- LastPass ( Best Encryption Software)
- KeePass
- Folder Lock
- DiskCryptor
- Cryptainer ( Best Encryption Software)
- Rohos Disk Encryption
- CryptoForge
- GNU Privacy Guard ( Best Encryption Software)
- BestCrypt
- Cryptainer
- McAfee Total Protection
30 Best Encryption Software For 2024
1. VeraCrypt ( Best Encryption Software)
VeraCrypt is a powerful open-source encryption software renowned for its robust security features and cross-platform compatibility. It offers strong encryption algorithms such as AES, Serpent, and Twofish, ensuring the confidentiality of sensitive data stored on various storage mediums, including hard drives, USB drives, and cloud storage.
VeraCrypt’s ability to create encrypted volumes and containers allows users to securely store and transport files and folders. Its plausible deniability feature enables users to create hidden volumes within encrypted containers, adding an extra layer of security against unauthorized access. Moreover, VeraCrypt’s support for multiple operating systems, including Windows, macOS, and Linux, makes it a versatile encryption solution for individuals and organizations seeking comprehensive data protection.
2. BitLocker
BitLocker is a native encryption feature integrated into Microsoft Windows operating systems, providing seamless data protection for Windows users. Utilizing AES encryption technology, BitLocker encrypts entire disk volumes, including system drives, external drives, and removable media, to safeguard data against unauthorized access and data breaches.
With its integration with Microsoft Active Directory, BitLocker enables centralized management of encryption policies and recovery keys, facilitating compliance with regulatory requirements. BitLocker’s transparent operation ensures minimal impact on system performance, allowing users to work seamlessly without compromising security. Furthermore, BitLocker’s support for hardware-based encryption technologies enhances data security and integrity, providing an additional layer of protection against sophisticated cyber threats.
3. AES Crypt
AES Crypt is a lightweight and easy-to-use encryption software designed to secure individual files with the Advanced Encryption Standard (AES) algorithm. Available for multiple platforms, including Windows, macOS, Linux, and Android, AES Crypt offers versatility and accessibility for users across different environments.
With its simple command-line interface and integration with file managers, AES Crypt enables users to encrypt files effortlessly, protecting them from unauthorized access and interception. AES Crypt’s strong encryption capabilities ensure the confidentiality and integrity of sensitive data, making it suitable for personal and professional use cases. Additionally, AES Crypt’s compatibility with third-party encryption software and services enhances its interoperability and usability, providing users with a flexible encryption solution to meet their data protection needs.
4. 7-Zip ( Best Encryption Software)
7-Zip is a popular open-source file archiver with built-in encryption capabilities, offering users a convenient way to compress and secure files and folders. Utilizing AES-256 encryption, 7-Zip encrypts archives with a password, ensuring that only authorized users can access the contents. 7-Zip’s support for multiple compression formats, including ZIP, TAR, and RAR, enhances its versatility and compatibility with various operating systems and file systems.
With its intuitive user interface and seamless integration with Windows Explorer, 7-Zip enables users to encrypt and decrypt files with ease. Moreover, 7-Zip’s lightweight design and efficient compression algorithms minimize storage space and optimize file transfer speeds, making it an ideal choice for users seeking a reliable encryption solution for file archiving and sharing.
5. GPG Suite
GPG Suite is a comprehensive encryption software suite designed to provide users with robust email and file encryption capabilities on macOS. Featuring GNU Privacy Guard (GPG) technology, GPG Suite enables users to encrypt, decrypt, sign, and verify emails and files using OpenPGP encryption standards.
With its integration with macOS Mail and Apple Mail, GPG Suite seamlessly integrates encryption features into users’ existing email workflows, ensuring secure communication and data privacy. GPG Suite’s intuitive interface and key management tools simplify the process of generating and managing encryption keys, making it accessible to users with varying levels of technical expertise. Additionally, GPG Suite’s support for file encryption and decryption allows users to protect sensitive files and folders stored on their Mac computers, enhancing overall data security and confidentiality. Overall, GPG Suite provides macOS users with a comprehensive and user-friendly encryption solution to safeguard their digital communications and files.
6. Symantec Endpoint Encryption
Symantec Endpoint Encryption is a comprehensive data protection solution designed for enterprise environments, offering robust encryption features to safeguard sensitive information across endpoints. With its centralized management console, Symantec Endpoint Encryption enables administrators to enforce encryption policies, manage encryption keys, and monitor compliance across distributed IT infrastructures.
Utilizing strong encryption algorithms such as AES and RSA, Symantec Endpoint Encryption encrypts data at rest, in transit, and on removable media, mitigating the risks of data breaches and unauthorized access. Its integration with Symantec Data Loss Prevention (DLP) technology enhances data security by preventing the leakage of sensitive information. Moreover, Symantec Endpoint Encryption’s support for multi-factor authentication and pre-boot authentication strengthens access controls, ensuring only authorized users can access encrypted data. Overall, Symantec Endpoint Encryption provides organizations with a scalable and robust solution to protect their critical data assets and maintain regulatory compliance in today’s dynamic threat landscape.
7. FileVault (for macOS)
FileVault is a native encryption feature integrated into macOS, providing seamless data protection for Mac users. Leveraging AES encryption technology, FileVault encrypts the entire disk volume, including the user’s home directory and system files, to safeguard data against unauthorized access and data breaches.
With its transparent operation, FileVault encrypts and decrypts data on-the-fly, ensuring minimal impact on system performance. FileVault’s integration with macOS authentication mechanisms, such as user passwords and recovery keys, enhances access controls and data security. Moreover, FileVault’s support for hardware-based encryption technologies further strengthens data protection, providing an additional layer of defense against sophisticated cyber threats. Overall, FileVault offers Mac users a convenient and effective way to encrypt their data and protect their privacy in today’s digital age.
8. Kleopatra ( Best Encryption Software)
Kleopatra is a user-friendly encryption software designed to provide individuals and organizations with OpenPGP encryption capabilities on Windows systems. With its intuitive interface and comprehensive features, Kleopatra enables users to generate encryption keys, encrypt and decrypt files, and sign and verify digital signatures easily. Leveraging the OpenPGP standard, Kleopatra ensures compatibility with other OpenPGP-compliant encryption software and services, enhancing interoperability and usability.
Its key management tools facilitate the creation, import, and export of encryption keys, allowing users to manage their cryptographic identities effectively. Moreover, Kleopatra’s integration with popular email clients, such as Microsoft Outlook and Mozilla Thunderbird, enables users to encrypt and sign emails securely, protecting sensitive communication from interception and tampering. Overall, Kleopatra provides users with a versatile and user-friendly encryption solution to safeguard their digital communications and files.
9. Boxcryptor
Boxcryptor is a cross-platform encryption software designed to secure files stored in cloud storage services such as Dropbox, Google Drive, and Microsoft OneDrive. With its seamless integration with popular cloud storage providers, Boxcryptor encrypts files locally before they are uploaded to the cloud, ensuring end-to-end encryption and data privacy. Boxcryptor’s support for AES encryption technology and zero-knowledge architecture ensures that only authorized users have access to encrypted data, protecting it from unauthorized access and data breaches.
Its user-friendly interface and intuitive file browser integration make it easy for users to encrypt, decrypt, and manage encrypted files across devices and platforms. Moreover, Boxcryptor’s multi-platform compatibility, including Windows, macOS, iOS, and Android, ensures flexibility and accessibility for users with diverse computing environments. Overall, Boxcryptor provides individuals and organizations with a convenient and effective solution to protect their sensitive data stored in the cloud.
10. Tutanota
Tutanota is an encrypted email service designed to provide users with secure communication and data privacy. Leveraging end-to-end encryption and zero-knowledge architecture, Tutanota encrypts all emails and attachments stored on its servers, ensuring that only the sender and recipient can access the contents. Tutanota’s web-based interface and mobile apps offer users a seamless and intuitive email experience, with built-in encryption features to protect sensitive communication from interception and surveillance. Its support for two-factor authentication and password-protected encryption keys enhances access controls and data security.
Moreover, Tutanota’s commitment to privacy and transparency, including its open-source codebase and adherence to strict privacy policies, instills trust and confidence in users concerned about their digital privacy. Overall, Tutanota provides individuals and businesses with a secure and privacy-focused email solution to communicate and collaborate with confidence in today’s digital world.
11. ProtonMail
ProtonMail is a renowned encrypted email service designed to prioritize user privacy and security. Operating on a zero-access encryption model, ProtonMail ensures that user emails are end-to-end encrypted, meaning only the sender and recipient have access to the content. ProtonMail’s strong encryption protocols and zero-knowledge architecture ensure that even the service provider cannot access user data.
With features like self-destructing emails, two-factor authentication, and built-in phishing protection, ProtonMail offers users a secure email experience without compromising convenience. Its user-friendly interface and cross-platform compatibility make it accessible to users across various devices and operating systems. ProtonMail’s commitment to privacy and transparency has made it a trusted choice for individuals and businesses seeking secure email communication in today’s digital landscape.
12. NordLocker ( Best Encryption Software)
NordLocker is a user-friendly encryption software designed to protect files stored on users’ devices and cloud storage services. With its strong encryption algorithms and zero-knowledge architecture, NordLocker ensures that only authorized users have access to encrypted files. Users can easily encrypt individual files or entire folders with a simple drag-and-drop interface, making data protection effortless.
NordLocker’s seamless integration with popular cloud storage providers like Dropbox, Google Drive, and OneDrive allows users to encrypt files before uploading them to the cloud, ensuring end-to-end encryption and data privacy. With features like file versioning, secure file sharing, and offline access, NordLocker offers users a comprehensive solution to protect their sensitive data from unauthorized access and data breaches.
13. Cryptomator
Cryptomator is an open-source encryption software designed to provide users with transparent, client-side encryption for their cloud storage services. With Cryptomator, users can create encrypted vaults on their local devices, encrypting files before they are uploaded to the cloud.
Utilizing strong encryption algorithms like AES and RSA, Cryptomator ensures that only authorized users have access to encrypted files, even when stored in the cloud. Its user-friendly interface and cross-platform compatibility make it accessible to users across various devices and operating systems. Cryptomator’s transparent encryption process allows users to work with their files as they normally would, without needing to worry about encryption and decryption processes. With its commitment to open-source development and privacy-focused design, Cryptomator provides users with a reliable and transparent solution to protect their sensitive data in the cloud.
14. Enigmail
Enigmail is a popular encryption extension for Mozilla Thunderbird, designed to provide users with seamless integration of OpenPGP encryption into their email workflow. With Enigmail, users can encrypt and sign emails using the OpenPGP standard, ensuring end-to-end encryption and data privacy.
Enigmail’s user-friendly interface and intuitive encryption key management make it easy for users to send encrypted emails to recipients, protecting sensitive communication from interception and surveillance. With features like automatic encryption, key management, and integrated support for encryption plugins like GnuPG, Enigmail offers users a comprehensive solution for secure email communication within the Thunderbird email client. Its commitment to open-source development and community-driven support has made it a popular choice for individuals and businesses seeking to enhance their email security and privacy.
15. PGP Desktop
PGP Desktop is a comprehensive encryption software suite designed to provide users with robust data protection capabilities for their files, emails, and entire disk volumes. With PGP Desktop, users can encrypt files and folders with strong encryption algorithms like AES and RSA, ensuring that only authorized users have access to sensitive data. PGP Desktop’s seamless integration with popular email clients like Microsoft Outlook and Apple Mail allows users to encrypt and sign emails using the OpenPGP standard, ensuring end-to-end encryption and data privacy.
Its centralized management console and policy-based encryption enable organizations to enforce encryption policies, manage encryption keys, and monitor compliance across distributed IT infrastructures. PGP Desktop’s support for disk encryption and removable media encryption further enhances data security, protecting sensitive information from unauthorized access and data breaches. Overall, PGP Desktop provides users with a comprehensive encryption solution to safeguard their data and ensure compliance with regulatory requirements in today’s digital landscape.
16. DiskCryptor ( Best Encryption Software)
DiskCryptor is an open-source disk encryption software designed to provide users with robust data protection for their entire disk volumes. With DiskCryptor, users can encrypt disk partitions or entire disks using strong encryption algorithms like AES, Twofish, and Serpent, ensuring the confidentiality and integrity of sensitive data.
DiskCryptor’s transparent encryption process encrypts data on-the-fly, allowing users to access encrypted volumes seamlessly without compromising performance. Its intuitive interface and straightforward operation make it accessible to users with varying levels of technical expertise. Despite being discontinued, DiskCryptor is still utilized by some users due to its reliability, security, and open-source nature. However, users should be cautious when using discontinued software and consider alternative encryption solutions with active development and support.
17. AxCrypt
AxCrypt is a user-friendly encryption software designed to provide individuals and businesses with easy-to-use file encryption capabilities. With AxCrypt, users can encrypt individual files or folders with a simple right-click interface, making data protection effortless. Utilizing strong encryption algorithms like AES-256, AxCrypt ensures that only authorized users have access to encrypted files. Its seamless integration with cloud storage providers like Dropbox, Google Drive, and Microsoft OneDrive allows users to encrypt files before uploading them to the cloud, ensuring end-to-end encryption and data privacy. AxCrypt’s multi-platform compatibility, including Windows, macOS, Android, and iOS, ensures flexibility and accessibility for users across various devices and operating systems. Overall, AxCrypt provides users with a user-friendly and effective solution to protect their sensitive data from unauthorized access and data breaches.
18. TrueCrypt (discontinued but still used by some)
TrueCrypt was a popular open-source disk encryption software known for its strong encryption capabilities and cross-platform compatibility. Despite being discontinued, TrueCrypt is still used by some users due to its reliability and security features. TrueCrypt allowed users to create encrypted volumes or encrypt entire disk partitions using encryption algorithms like AES, Serpent, and Twofish, ensuring data confidentiality and integrity.
However, since TrueCrypt is no longer maintained or supported, users should exercise caution when using it and consider migrating to alternative encryption solutions with active development and support. While TrueCrypt may still function adequately for some users, the lack of updates and security patches may pose risks in terms of compatibility, interoperability, and vulnerability to emerging security threats.
19. Sophos SafeGuard Encryption
Sophos SafeGuard Encryption is a comprehensive encryption solution designed to provide organizations with robust data protection capabilities for their endpoints and sensitive data assets. With Sophos SafeGuard Encryption, organizations can encrypt entire disk volumes, individual files, removable media, and email communications, ensuring end-to-end encryption and data privacy. Its centralized management console enables administrators to enforce encryption policies, manage encryption keys, and monitor compliance across distributed IT infrastructures. Sophos SafeGuard Encryption’s support for multi-factor authentication, pre-boot authentication, and hardware-based encryption technologies enhances access controls and data security. Moreover, its integration with endpoint security solutions like antivirus and data loss prevention (DLP) further strengthens data protection and threat mitigation capabilities. Overall, Sophos SafeGuard Encryption provides organizations with a comprehensive and effective solution to protect their sensitive data and ensure compliance with regulatory requirements in today’s evolving threat landscape.
20. LastPass ( Best Encryption Software)
LastPass is a popular password management solution designed to provide users with secure storage and management of their passwords and sensitive information. While not strictly an encryption software, LastPass utilizes strong encryption algorithms to encrypt user passwords and data stored within its vault. With LastPass, users can generate and store complex passwords for their online accounts, eliminating the need to remember multiple passwords.
LastPass’s browser extensions and mobile apps allow users to access their passwords across various devices and platforms securely. Its features like password sharing, secure notes, and multi-factor authentication enhance usability and security. While LastPass primarily focuses on password management, its encryption capabilities ensure that user data remains protected against unauthorized access and data breaches. Overall, LastPass provides users with a convenient and secure solution to manage their passwords and safeguard their digital identities in today’s interconnected world.
21. KeePass
KeePass is a popular open-source password manager designed to securely store and manage passwords and other sensitive information. Utilizing strong encryption algorithms such as AES and Twofish, KeePass encrypts user passwords and data stored within its database, ensuring that only authorized users have access. KeePass’s database is locked with a master password or key file, providing an additional layer of security. Its portable nature allows users to carry their encrypted password database on removable media or cloud storage services. With features like password generation, auto-type, and multi-factor authentication support, KeePass offers users a comprehensive solution for password management while prioritizing security and privacy. Its active development community and support for various platforms make it a versatile and reliable choice for individuals and organizations seeking to enhance their password security.
22. Folder Lock
Folder Lock is a comprehensive data security software designed to provide users with various encryption and protection features for their files, folders, and drives. With Folder Lock, users can encrypt and password-protect their files and folders, ensuring that only authorized users can access them. Folder Lock’s encryption algorithms, including AES and Blowfish, ensure data confidentiality and integrity. Additionally, Folder Lock offers features such as file shredding, secure backup, and portable lockers for encrypted data storage. Its intuitive interface and user-friendly operation make it accessible to users with varying levels of technical expertise. Folder Lock’s integration with cloud storage services and removable media enhances data protection and accessibility across devices and platforms. Overall, Folder Lock provides users with a comprehensive and effective solution to safeguard their sensitive data and ensure privacy in today’s digital age.
23. DiskCryptor
DiskCryptor is an open-source disk encryption software designed to provide users with robust data protection for their entire disk volumes. With DiskCryptor, users can encrypt disk partitions or entire disks using strong encryption algorithms like AES, Twofish, and Serpent, ensuring the confidentiality and integrity of sensitive data. DiskCryptor’s transparent encryption process encrypts data on-the-fly, allowing users to access encrypted volumes seamlessly without compromising performance. Its intuitive interface and straightforward operation make it accessible to users with varying levels of technical expertise. Despite being discontinued, DiskCryptor is still utilized by some users due to its reliability, security, and open-source nature. However, users should be cautious when using discontinued software and consider alternative encryption solutions with active development and support.
24. Cryptainer ( Best Encryption Software)
Cryptainer is a user-friendly encryption software designed to provide users with secure storage and encryption capabilities for their files and folders. With Cryptainer, users can create encrypted vaults or containers to securely store their sensitive data, ensuring data privacy and confidentiality. Utilizing strong encryption algorithms like AES and Blowfish, Cryptainer ensures that only authorized users have access to encrypted data. Its intuitive interface and drag-and-drop functionality make it easy for users to create, access, and manage encrypted containers. Additionally, Cryptainer offers features such as file shredding, secure email attachments, and password management. Its cross-platform compatibility and support for portable containers enhance data protection and accessibility across devices and platforms. Overall, Cryptainer provides users with a simple yet effective solution to protect their sensitive data and ensure privacy in today’s digital world.
25. Rohos Disk Encryption
Rohos Disk Encryption is a comprehensive disk encryption software designed to provide users with secure storage and encryption capabilities for their disk volumes. With Rohos Disk Encryption, users can create encrypted disk partitions or entire disks using strong encryption algorithms like AES and Blowfish, ensuring the confidentiality and integrity of sensitive data. Rohos Disk Encryption’s transparent encryption process encrypts data on-the-fly, allowing users to access encrypted volumes seamlessly without compromising performance. Its intuitive interface and user-friendly operation make it accessible to users with varying levels of technical expertise.
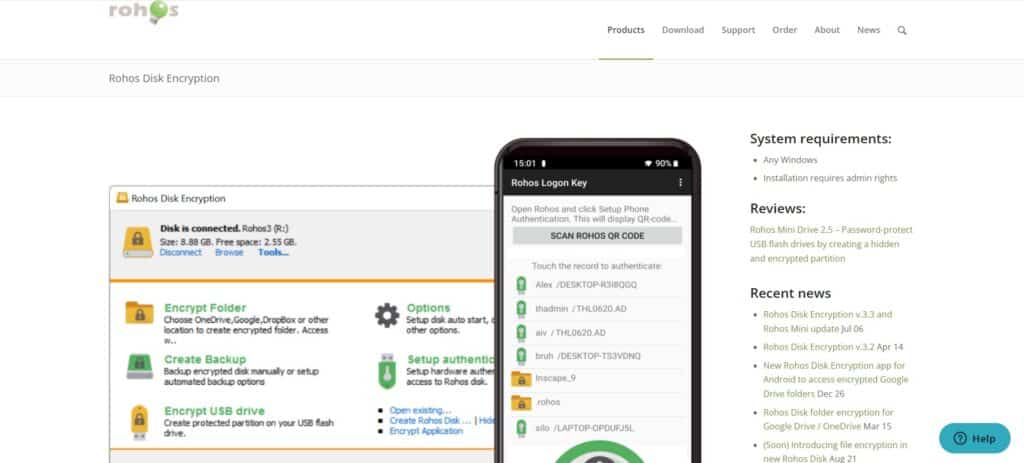
Additionally, Rohos Disk Encryption offers features such as USB key authentication, emergency recovery, and virtual keyboard protection. Its cross-platform compatibility and support for portable containers enhance data protection and accessibility across devices and platforms. Overall, Rohos Disk Encryption provides users with a reliable and effective solution to protect their sensitive data and ensure privacy in today’s digital age.
26. CryptoForge
CryptoForge is a comprehensive encryption software designed to provide users with robust data protection for their files and folders. With CryptoForge, users can encrypt files using strong encryption algorithms like AES, Blowfish, and TripleDES, ensuring the confidentiality and integrity of sensitive data. CryptoForge offers features such as file shredding, secure email attachments, and password management to enhance data security and privacy. Its intuitive interface and user-friendly operation make it accessible to users with varying levels of technical expertise. Additionally, CryptoForge offers support for creating self-extracting encrypted files, allowing users to securely share encrypted data with others. Its cross-platform compatibility and integration with cloud storage services enhance data protection and accessibility across devices and platforms. Overall, CryptoForge provides users with a comprehensive and effective solution to safeguard their sensitive data and ensure privacy in today’s digital age.
27. GNU Privacy Guard ( Best Encryption Software)
GNU Privacy Guard (GnuPG) is a free and open-source encryption software suite designed to provide users with secure communication and data protection capabilities. GnuPG implements the OpenPGP standard, enabling users to encrypt and sign emails, files, and communications securely. With its strong encryption algorithms and digital signature features, GnuPG ensures end-to-end encryption and data integrity. Its command-line interface and integration with email clients and applications allow users to encrypt and decrypt data seamlessly. Additionally, GnuPG offers features such as key management, key signing, and key revocation to enhance data security and privacy. Its cross-platform compatibility and extensive community support make it a versatile and reliable choice for individuals and organizations seeking to enhance their encryption capabilities.
28. BestCrypt
BestCrypt is a comprehensive encryption software solution designed to provide users with secure storage and encryption capabilities for their files, folders, and disk volumes. With BestCrypt, users can create encrypted containers or volumes using strong encryption algorithms like AES, Blowfish, and Twofish, ensuring data confidentiality and integrity. BestCrypt’s transparent encryption process encrypts data on-the-fly, allowing users to access encrypted volumes seamlessly without compromising performance. Its intuitive interface and user-friendly operation make it accessible to users with varying levels of technical expertise. Additionally, BestCrypt offers features such as file shredding, secure backup, and password management to enhance data security and privacy. Its cross-platform compatibility and support for portable containers enhance data protection and accessibility across devices and platforms. Overall, BestCrypt provides users with a comprehensive and effective solution to protect their sensitive data and ensure privacy in today’s digital age.
29. Cryptainer
Cryptainer is a user-friendly encryption software designed to provide users with secure storage and encryption capabilities for their files and folders. With Cryptainer, users can create encrypted vaults or containers to securely store their sensitive data, ensuring data privacy and confidentiality. Utilizing strong encryption algorithms like AES and Blowfish, Cryptainer ensures that only authorized users have access to encrypted data. Its intuitive interface and drag-and-drop functionality make it easy for users to create, access, and manage encrypted containers. Additionally, Cryptainer offers features such as file shredding, secure email attachments, and password management. Its cross-platform compatibility and support for portable containers enhance data protection and accessibility across devices and platforms. Overall, Cryptainer provides users with a simple yet effective solution to protect their sensitive data and ensure privacy in today’s digital world.
30. McAfee Total Protection
McAfee Total Protection is a comprehensive security suite designed to provide users with protection against various online threats, including viruses, malware, and identity theft. While not strictly an encryption software, McAfee Total Protection includes encryption features to help users protect their sensitive data and ensure privacy. With McAfee Total Protection, users can encrypt files and folders to prevent unauthorized access and data breaches.
Additionally, McAfee Total Protection offers features such as secure online storage, password management, and encrypted storage for sensitive files. Its intuitive interface and user-friendly operation make it accessible to users with varying levels of technical expertise. Overall, McAfee Total Protection provides users with a comprehensive solution to protect their devices and data from online threats and ensure privacy in today’s digital age.
Benefits of Best Encryption Software
The benefits of utilizing the best encryption software extend across various aspects of digital security and data protection. Firstly, encryption software ensures the confidentiality and privacy of sensitive information by converting it into an unreadable format that can only be deciphered with the appropriate decryption key. This encryption process mitigates the risk of unauthorized access, interception, or tampering, safeguarding data from cyber threats and data breaches.
Moreover, encryption software enhances data integrity by providing assurance that information remains unaltered during transmission or storage. By encrypting data, organizations can detect any unauthorized modifications or tampering attempts, thereby maintaining the integrity and authenticity of their information assets.
Another significant benefit of encryption software is its role in regulatory compliance. Many regulatory frameworks and industry standards require organizations to implement encryption measures to protect sensitive data and ensure compliance with data protection laws. By employing encryption software, organizations can demonstrate their commitment to compliance, mitigate the risk of regulatory penalties, and uphold the trust of customers and stakeholders.
Furthermore, encryption software fosters trust and confidence among users by providing assurance that their personal and sensitive information is secure. In an era where data privacy concerns are paramount, the implementation of robust encryption solutions helps organizations build trust with customers, partners, and employees, thereby enhancing brand reputation and loyalty.
Additionally, encryption software facilitates secure collaboration and communication by encrypting emails, files, and other communications exchanged between parties. This ensures that sensitive information remains confidential and protected from interception or eavesdropping, enabling secure collaboration across distributed teams and networks.
In summary, the benefits of the best encryption software include enhanced data security, confidentiality, and integrity, regulatory compliance, trust-building, and secure collaboration. By leveraging encryption solutions, organizations can protect sensitive information, mitigate risks, and uphold the trust and confidence of stakeholders in an increasingly interconnected and data-driven world.
Conclusion : Best Encryption Software
In conclusion, the utilization of the best encryption software stands as a cornerstone in the realm of digital security, offering a multitude of benefits that contribute to the protection, integrity, and confidentiality of sensitive information. By converting data into an unreadable format, encryption software ensures that it remains secure and inaccessible to unauthorized parties, mitigating the risks posed by cyber threats and data breaches.
The significance of encryption software extends beyond mere data protection, encompassing regulatory compliance, trust-building, and secure collaboration. Compliance with regulatory requirements is facilitated through the implementation of encryption measures, demonstrating organizations’ commitment to safeguarding sensitive data and upholding privacy laws. Moreover, encryption software fosters trust among customers, partners, and employees by providing assurance that their personal information is secure, thereby enhancing brand reputation and loyalty.
Furthermore, encryption software enables secure collaboration and communication by encrypting emails, files, and other communications, ensuring confidentiality and protection from interception or eavesdropping. This facilitates seamless collaboration across distributed teams and networks, enhancing productivity and efficiency in today’s interconnected digital environment.
In essence, the best encryption software plays a vital role in safeguarding sensitive information, ensuring regulatory compliance, fostering trust, and enabling secure collaboration. By leveraging encryption solutions, organizations can mitigate risks, protect valuable data assets, and navigate the complexities of the digital landscape with confidence and resilience.
FAQ’S : Best Encryption Software
What is encryption software?
Encryption software is a tool designed to encode sensitive data into an unreadable format, known as ciphertext, using encryption algorithms. This ensures that the information remains secure and confidential, even if intercepted.
Why do I need encryption software?
Encryption software is essential for protecting sensitive information from unauthorized access, interception, or tampering. It ensures data confidentiality, integrity, and privacy, especially in environments where data security is paramount.
How does encryption software work?
Encryption software utilizes mathematical algorithms to scramble plaintext data into ciphertext, making it unreadable without the corresponding decryption key. Only authorized parties with the key can decipher the ciphertext back into its original form.
Is encryption software legal?
Yes, encryption software is legal and widely used for securing data and communications. However, certain countries may have regulations regarding the export, use, or strength of encryption algorithms, so it’s essential to be aware of local laws and compliance requirements.
What types of data can encryption software protect?
Encryption software can protect various types of data, including files, emails, instant messages, databases, and sensitive communications exchanged over networks or stored on devices.
Can encryption software be decrypted?
Encryption software can only be decrypted by authorized parties with the corresponding decryption key. Without the key, decrypting encrypted data is computationally infeasible, ensuring its security.
Is encryption software compatible with different platforms?
Yes, many encryption software solutions are compatible with multiple platforms, including Windows, macOS, Linux, iOS, and Android, ensuring seamless integration and accessibility across diverse environments.
How strong is encryption software against cyber threats?
The strength of encryption software depends on the encryption algorithms used and their implementation. Advanced encryption standards (AES) and other robust algorithms provide strong protection against cyber threats and data breaches when implemented correctly.